
TLS 1.3 – Enhanced Performance, Hardened Security
While TLS 1.2 has served honorably all these years, TLS 1.3 is provably more secure and efficient. TLS 1.3 has been extensively tested in experimental browser implementations, and it is now ready to replace TLS 1.2 as the network security protocol of choice. Publishing TLS 1.3 is a big step closer towards a faster and safer Internet for all.
Are you taking advantage of TLS 1.3 enhanced performance and security? TLSv.13 Released on 2017 and many of the websites are already adopted it .
If you are the owner of any website plan to migrate TLS protocol to support the strongest one .
To migrate to TLSv1.3 one should know the underline technology supports the latest protocol and also the the client that is used to access the site is compatible with TLSv1.3 .
For JAVA Note that TLS 1.3 support is available in WebLogic Server 12.2.1.4 or 12.2.1.3 with JDK 8 u261+.
Browsers that support the TLS version are given in the below screen

If the server side is updated to the latest protocols then make sure the client are supported to TLSv1.3 for the better performance and security .
Performance has a major impact on user experience. TLS 1.3 represents a pivotal turning point for HTTPS performance.
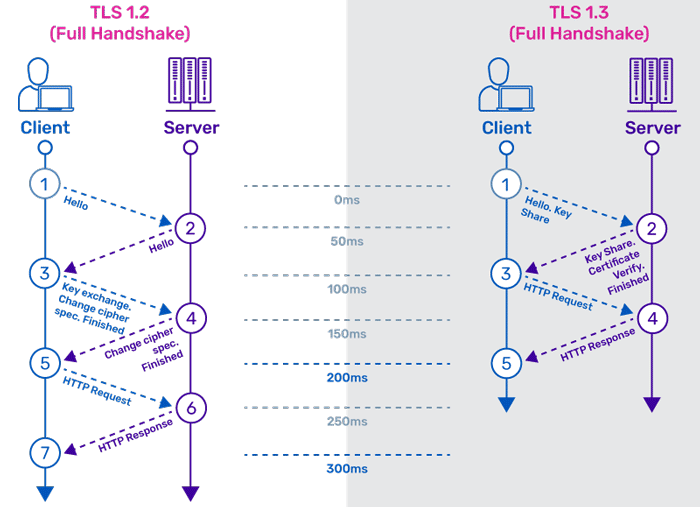
TLS v1.2 vs TLS v1.3
TLS 1.3 offers several improvements over earlier versions, most notably a faster TLS handshake and simpler, more secure cipher suites and zero round trip time .key exchanges further streamline the TLS handshake. Together, these changes provide better performance and stronger security. you can see the list of activities that are performed during SSL handshake are minimized as a result it produces very high speed for the client . At the same time security is also dealt with utmost priority as a result it provide highest level of security and better performance then the older protocols .
Here we will see for various Server Technologies (Middleware ) ,how we enable TLSv1.3 and disable all the other lower protocols.
IBM JAVA Supports TLSv1.3 from JDK 8 SR6 FP25 (8.0.6.25) onwards
How to Enable TLSv1.3 in Weblogic Application server ??
TLS 1.2 is the default minimum protocol version configured in WebLogic Server 14.1.1. TLS 1.3 support is available in WebLogic Server versions that are certified with Java SE implementations supporting TLS 1.3 in JSSE. e.g., TLS 1.3 support is available in WebLogic Server 14.1.1 when using Java SE 11 or JDK 8 u261+.
Note that TLS 1.3 support is available in WebLogic Server 12.2.1.4 or 12.2.1.3 with JDK 8 u261+.
We can disable old version by setting up minimum supported protocol in JAVA_OPTS
-Dweblogic.security.SSL.minimumProtocolVersion=TLSv1.3
Note the above setting is only affects inbound connections. If we have an application on Weblogic making outbound call to other applicaiton (ex Ldap ) then look for below section .
For Outbound Connections
To control the outbound connections the following JAVA_OPTIONS system property is available:
Example to allow all TLS protocols for the most common SSLSocket or SSLSocketFactory classes:
-Djdk.tls.client.protocols=TLSv1.3Applications using the HttpsClient or HttpsURLConnection classes can use the https.protocols system property:
-Dhttps.protocols=TLSv1.3How to Enable TLSv1.3 in Jboss Application server ??
In JBOSS to update TLSv1.3 either change in jdk lever or update doamin.xml or standalone.xml based on the configuration used .
On EAP 6.4 update below ssl config
<server-identities>
<ssl>
<engine enabled-protocols="TLSv1.1 TLSv1.2" />
<keystore ... />
</ssl>On 7.X run below CLI command or just update ssl tag as give enabled-protocols to TLSv1.3 .
/core-service=management/security-realm=RealmName/server-identity=ssl/:write-attribute(name=enabled-protocols,value=["TLSv1.3"])save the changes and restart the jboss services .
How to Enable TLSv1.3 in Apache Web/httpd server ??
To support TLSv1.3 first httpd need to be upgraded to 2.4.38 . Lower versions does not support TLSv1.3 protocol .So take the advantage of TLSv1.3 let upgrade the httpd first then plan for changing the protocols
Enabling the TLSv1.3 protocol is very easy in httpd server . Let look into it .
Login to the server and take httpd.conf or ssl.conf file where ever ssl was configured . Locate SSLProtocol and modify the value as given below and save the file . Now restart the httpd service to take affect the changes .
SSLProtocol -all +TLSv1.3How to Enable TLSv1.3 in WebSphere Application server ??
TLS v 1,3 supported starting from 9.0.5.2 . Follow below steps to configure TLSv1.3 in WebSphere .
1. Log in to the WebSphere Application Server Integrated Solutions Console.
2. Click Security > SSL certificate and key management, and under Related Items, click SSL configurations. (such as CellDefaultSSLsetting , NodedefaultSSLsetting and any other SSLConfig )
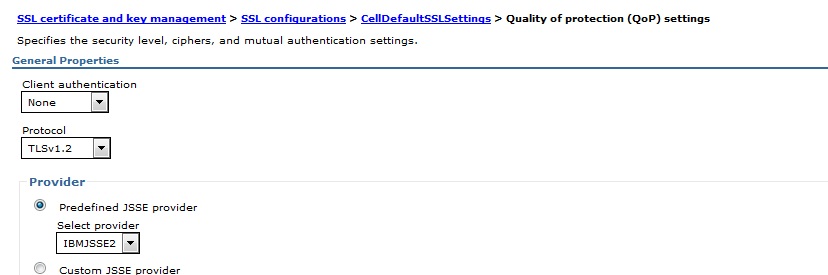

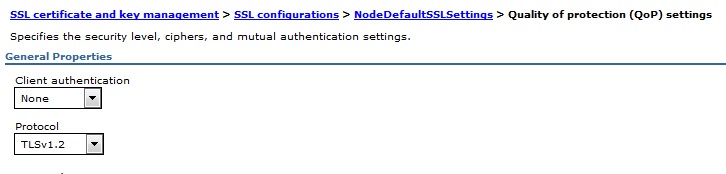
Note: For each node it has their own NodeDefaultSSLsetting and above setting will APPLY BOTH inbound and outbound SSL Communication .
In the above figures TLSv1.2 is there but in our case we should select TLSv1.3 .
3. Select each SSL Configuration described above, then click Quality of protection (QoP) settings under Additional Properties.
4. On the Quality of protection (QoP) settings panel, select TLSv1.3 from the pull-down list in the box named Protocol. change the protocol to TLSV1.3
5. Click Apply and Save.
For the WAS WebServer Plug-in, TLS 1.3 must be explicitly enabled by setting global <Config> property in plugin-cfg.xml to specify 'UseTLS13="true"'.
How to Enable TLSv1.3 in JDK ??
Edit the <java-home>/lib/security/java.security in JDK 8 and earlier) and add TLS 1.1 and TLS 1.2 to the jdk.tls.disabledAlgorithms property by appending
TLSv1, TLSv1.1 ,TLSv1.2
For example, if the current value is:
jdk.tls.disabledAlgorithms=SSLv3, RC4, DES, MD5withRSA, DH keySize < 1024, \
EC keySize < 224, 3DES_EDE_CBC, anon, NULL
then the new value would be:
jdk.tls.disabledAlgorithms=SSLv3, RC4, DES, MD5withRSA, DH keySize < 1024, \ EC keySize < 224, 3DES_EDE_CBC, anon, NULL, TLSv1, TLSv1.1, TLSv1.2
How to Enable TLSv1.3 in Tomcat server ??
Edit TOMCAT_HOME/conf/server.xml config file
Tomcat 5 & 6 (Prior to 6.0.38)
Within the server.xml, locate the sslProtocols entry and make sure only TLS 1.2 protocol is specified:
sslProtocols = “TLSv1.2”
Tomcat 6 & 7 (6.0.3.8 and newer)
Within the server.xml file, locate the sslEnabledProtocols entry and make sure only TLS 1.2 protocol is specified:
sslEnabledProtocols = “TLSv1.2”
Restart the Tomcat service to complete the changes and verify .
Verifying the website to see the Protocols enabled ??
SSL Labs is one of the way to verify the Web URL’s for the enabled protocols . Let see for our askmiddlewareexpert.com domain . go to https://www.ssllabs.com/ssltest/


These are the result of ssllabs scan . At the moment TLSv1.3 is not enabled for askmiddlewareexpert.com hence the results shown No for TLSv1.3
We can also verify using openssl with the below snippet.
openssl s_client -connect SERVERIP:PORT tls1_3
Sharing is Caring 🙂 Happy Learning …
